
After long time, over this weekend i participated in a CTF - VishwaCTF-2024, it was beginner freindly CTF where i solved some challenges over there, Below is the writeup for the challenges that I managed to solve.
All challenges can be found here
Web
Save The City
Description
The RAW Has Got An Input That ISIS Has Planted a Bomb Somewhere In The Pune! Fortunetly, RAW Has Infiltratrated The Internet Activity of One Suspect And They Found This Link. You Have To Find The Location ASAP!
after opening the site i stumbled upon blank page where was nothing but just “libssh_0.8.1” so i googled exploit for this particular version where i got to know that it is vulnerable to Authentication Bypass (CVE-2018-10933) vuln and got this page where
Exploit
1 | import sys |
after ls’ing the dir we got the flag
1 | python solve.py "cat secret.txt/flag.txt" |
Trip To Us
Description
IIT kharakpur is organizing a US Industrial Visit. The cost of the registration is $1000. But as always there is an opportunity for intelligent minds. Find the hidden login and Get the flag to get yourself a free US trip ticket.
it was typical SQLi bypass challenge, using admin” or “1”=”1”– as username and password i did able to bypass it.
They Are Coming
Description
Aesthetic Looking army of 128 Robots with AGI Capabilities are coming to destroy our locality!
Nothing interesting on home page at first glance, looking at source code got a js file where some bottom portion of code caught my attention after beautifying it
1 | yt = () => { |
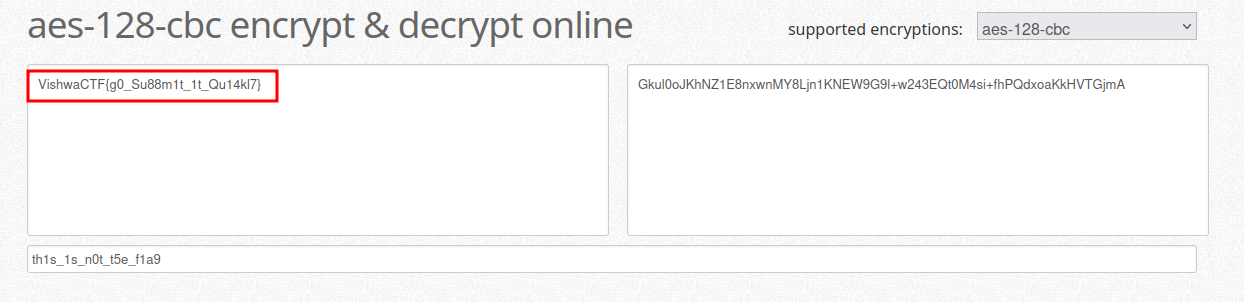
so as we can see here some data being stored on local storage and moreover more interesting one is Flag item that has some encrypted value
hmm, so most probably this one is a real flag that is encrypted using key? , if so which encryption standard and key?.
so about encryption algorithm we got some hints already, if you look on above code there is children key with value I have done 128 cbc tests so its most likely AES 128 CBC
and about key? so if we check robots.txt we all sorted out
1 | User-agent: * |
now we have Decryption key and cipher as well we are ready to go to this site and we got the flag.
OSINT
The end is beginning
Description
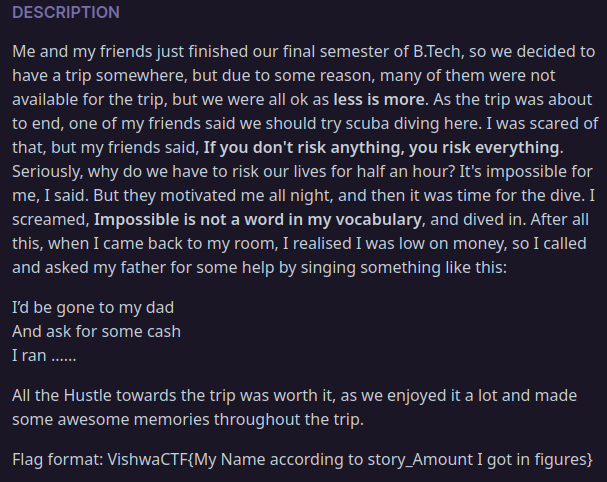
searching for
1 | I’d be gone to my dad |
shows me a rap song results, maybe its connected to lyrics of this particular song, so going through lyrics i figured out second portion of flag that is
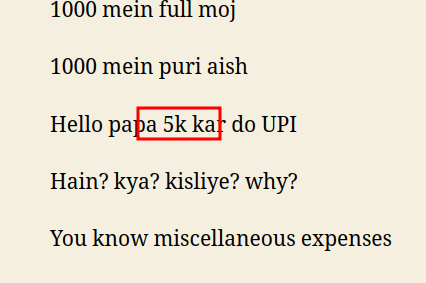
and the first part was name of song i.e. Pradox so th flag will be
VishwaCTF{Paradox_5000}
TRY HACK ME
Discription
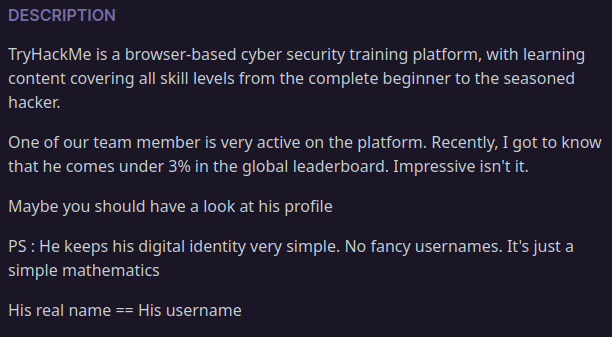
as description says one of the team member, i went straight through their official page where they have page for thier team members in the bottom
after checking each member profile with their username one of them have same ranking as mentioned and flag mentioned in description as well.
ifconfig_inet
Description

hmm, sound familiar though. okay reading all description i searched for this
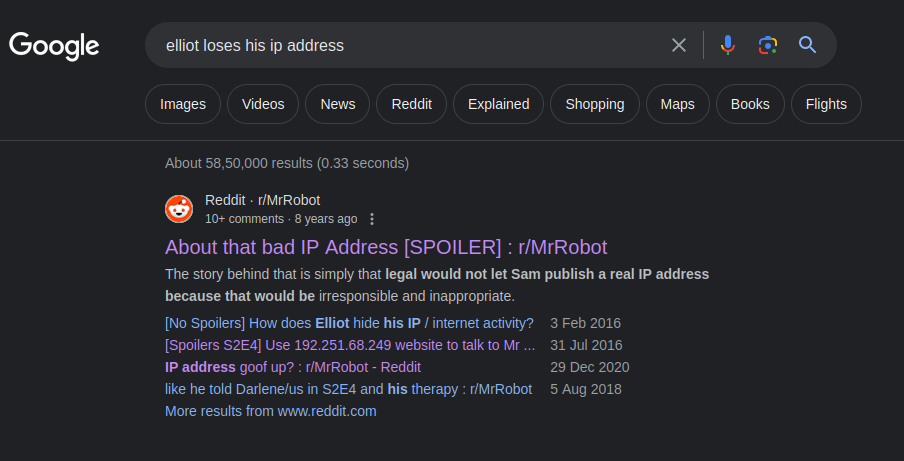
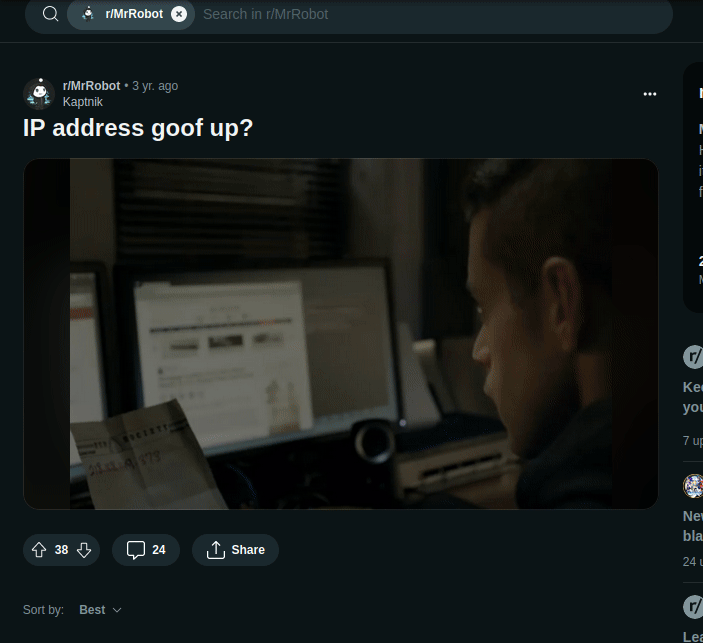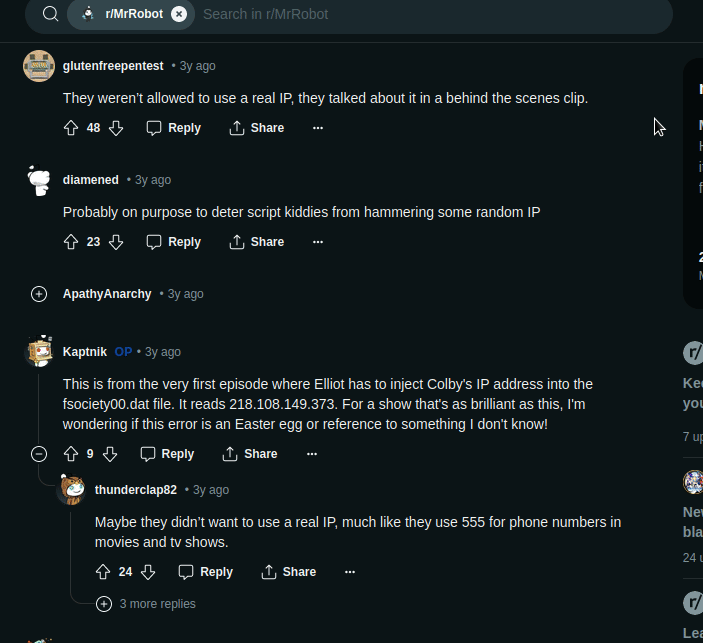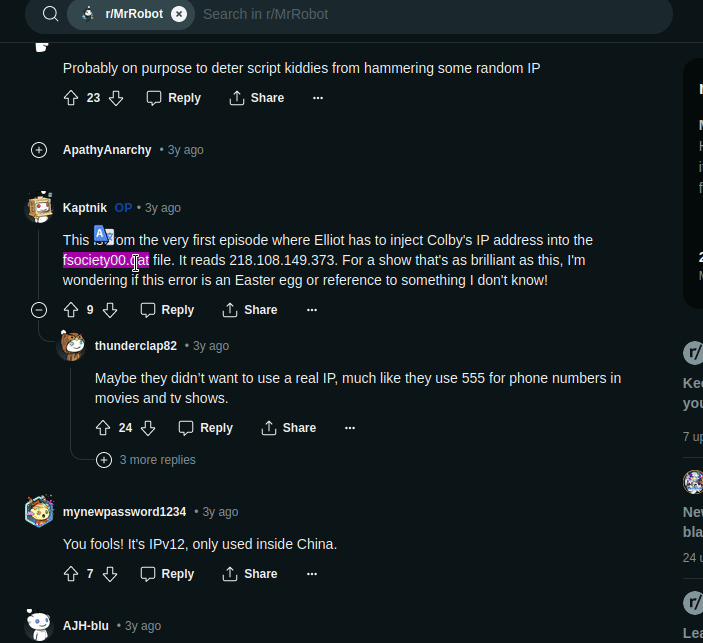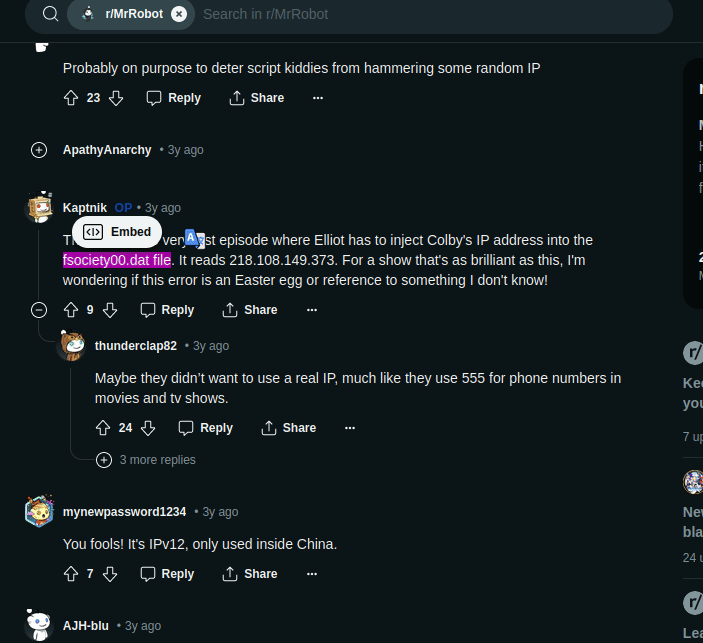
as we can see we got some reddit pages that is about some IP address( BTW this challenge is ragarding a famous television series Mr. Robot so if you have watched it, it may give you some insights)
i got this image
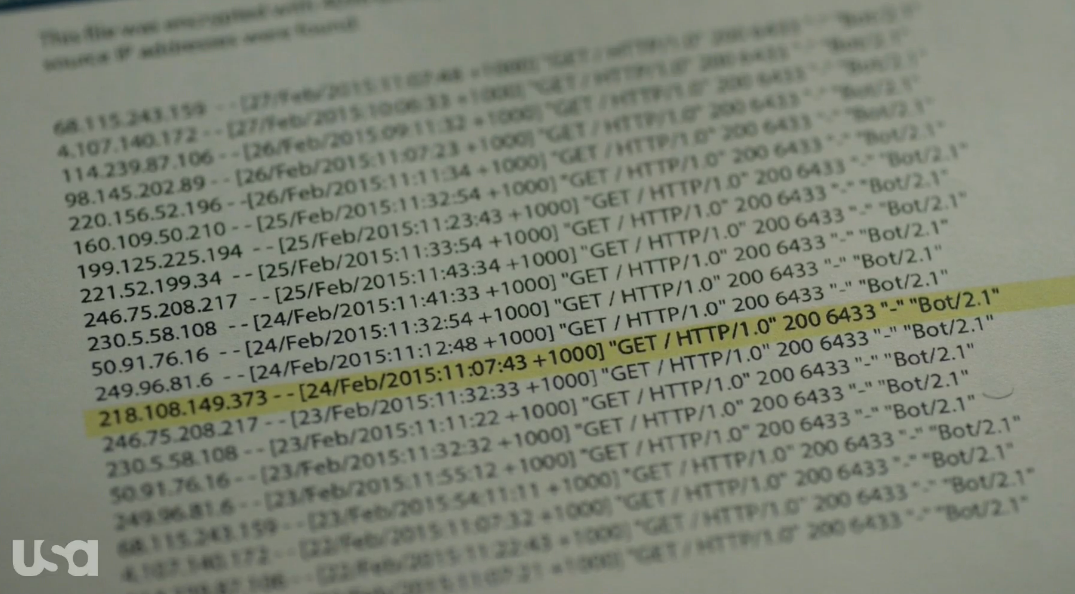
so maybe the highlighted one is what we searching for but still left with the .dat file that is first half our flag, searching more gives me this page
and here some people were talking about IP addresses, reading their chat i got the file name i.e. fsociety00.dat
so flag is
VishwaCTF{fsociety00.dat_218.108.149.373}
Post CTF
Steg
We Are Valorant
Description
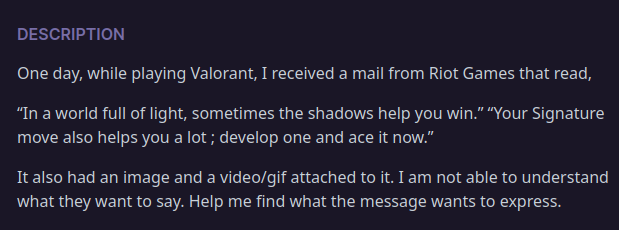
we have given two file i.e. we_are_valorant.adts and Astra_!!.mp4, after checking the format of .adts using file command it shows its jpg one
after changing its magic numbers to jpg it turns out as valorant theme jpg file, i tried getting some info from this file but no use and also uploaded it to the Aperi site but got nothing.
but when i changed the extension of original one i.e. we_are_valorant.adts to .jpg and uploaded it there then there were some Comman Passwords i.g. Tenz, tenz, From the shadows, Dissipate, dissipate, Kyedae, kyedae
using steghide with first password that is Tenz extracts a file not_a_secret.txt that contains the flag.
VishwaCTF{you_are_invited_to_the_biggest_valorant_event}
Mysterious Old Case
Description
You as a FBI Agent, are working on a old case involving a ransom of $200,000. After some digging you recovered an audio recording.
here we given final.mp3 and upon checking its exif we got this
1 | ExifTool Version Number : 12.65 |
here are some exif infos that caught my attention i.e. Genre, Band, Comment and User Defined URL, in URL we have given drive file link that is log zip file named flight_logs.zip that is encrypted.
and comments says password for the zip is all lowecase with no spaces but we don’t even have password till now
and if you see Band it has value DB Cooper i searched it on google and got to know that its a person name who hijacked Northwest Orient Airlines Flight 305, a Boeing 727 aircraft, in United States airspace on November 24, 1971.
and because our file name is flight_log.zip its connecting our insights that we are in right directions
i tried some passwords from exif info but no use but i had all info about DB Cooper in wikipedia the major one is the one that i mentioned above so then i tried name of the flight that is Northwest Orient Airlines Flight as passsword northwestorientairlines and it worked indeed.
now if we look inside folder we have thousand of log file and thats intimidating but there very simple logic of mine worked, that is i sorted out all the file on the basis of their size i.e.
1 | └─$ ls -lSh | head |
so if you look at the list the first one is Flight-305.log and thats the desired one
and i contains around some 30,0000 lines if you scroll it gradually you’ll gonna see the part of flag, so either we can grab it one by one or filter it using regex and tr e.g.
1 | └─$ grep -v '^1971-11-24.*727$' Flight-305.log | tr '\n' ' ' | tr -d ' ' |
BTW we could have find the targeted log file simply by the number of filght that is mentioned in wikipedia i.e. Flight 305
Secret Code
Description
Akshay has a letter for you and need your help
two files confidential.jpg and letter.txt
cating letter.txt says
1 | To, |
no useful information here, then i started working on jpg file and if you see below using strings shows it contains some more files inside itself , you can extract it is using foremost and some time unzip works as well.
1 | └─$ strings -10 confidential.jpg |
so here helper.txt says
1 | └─$ cat helper.txt |
now 5ecr3t_c0de.zip is protected and password possiblity is any 6 digit numbers within 999999 we can brute force it using john
script for generating all possible 6 digits numbers
1 | def generate_combinations(): |
john command
1 | ┌──(zr0x㉿pwn3r)-[~/…/vishwaCTF-2024/steg/03_Secret_Code/tmp] |
after unzipping we got two files i.e. 5ecr3t_c0de.txt and info.txt
info.txt
1 | What are these random numbers? Is it related to the given image? Maybe you should find it out by yourself |
5ecr3t_c0de.txt
1 | └─$ cat 5ecr3t_c0de.txt|head |
so if see info and 5ecr3t_c0de we can infer that given numbers are the coordinates likely indicate positions of pixels within the image.
they are probably in (x, y) order, representing horizontal (x) and vertical (y) coordinates. or height and width sequentially.
so anticipation is that we have given a blank black jpg images and these are flag coordinates which will create or show flag and most probably in white
we can use this script for that
1 | from PIL import Image |
and here we go

OSINT
Sagar Sangram
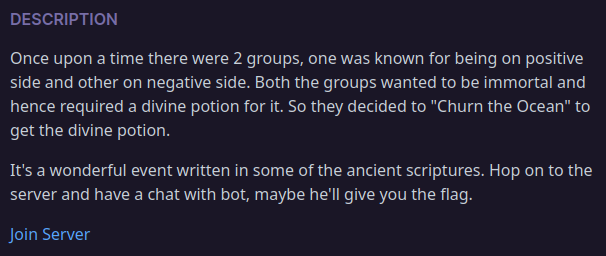
with that sort tale description we have given descord server to join as well.
so if you are indian and know Indian mythological story then after reading this you’ll figure it aobut instantly that here its about The Samudra Manthana that is a major episode in Hinduism that is elaborated in the Vishnu Purana, a major text of Hinduism.
so when hop in the server we have given some instruction in rule section where we have to chat with a bot and answer some questions that is all regarding Samudra Manthana and if you manage to answer those all we will be given the flag at last.
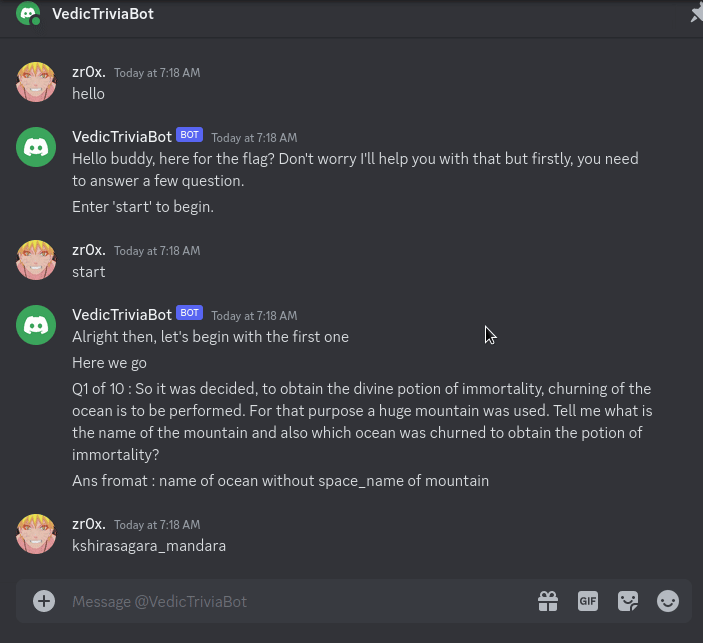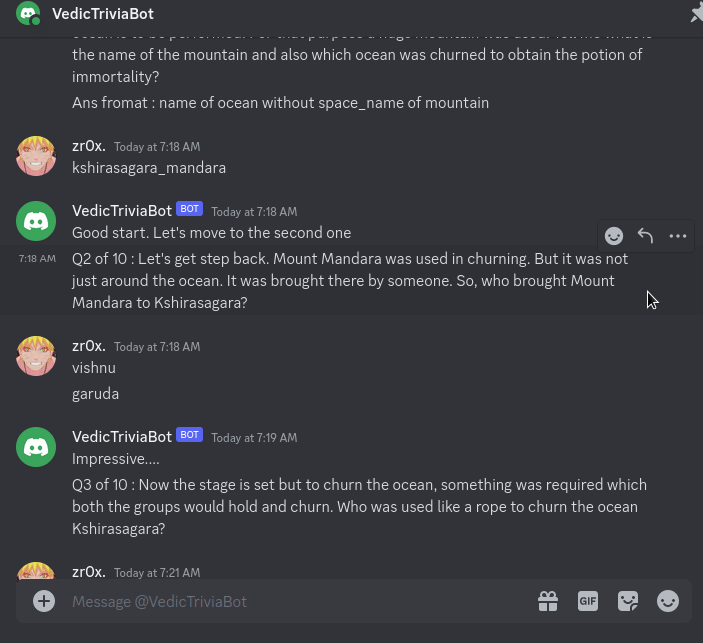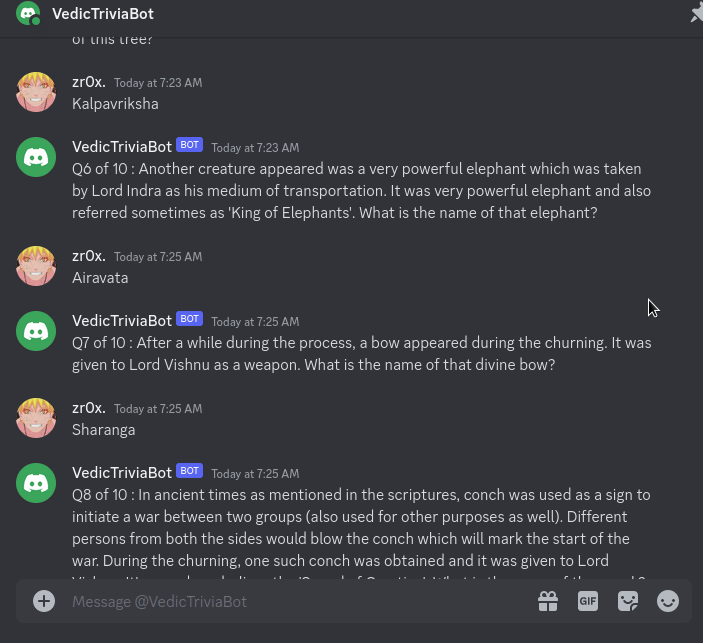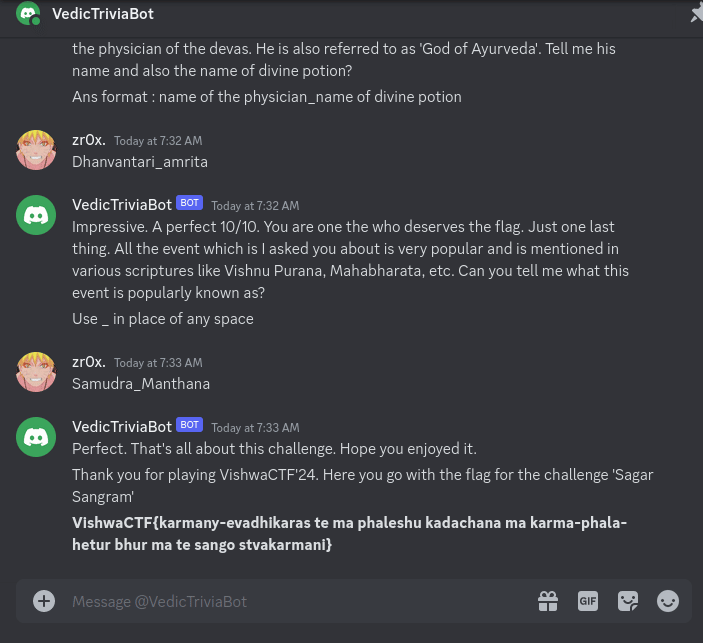
Flag :
VishwaCTF{karmany-evadhikaras te ma phaleshu kadachana ma karma-phala-hetur bhur ma te sango stvakarmani}
Forensics
yet to do …………